Get the job you really want.
Maximum of 25 job preferences reached.
Top Remote Cyber Security Jobs in Memphis, TN
Computer Vision • Information Technology
Perform penetration testing on web applications and networks, discover vulnerabilities, develop tools, and manage projects while contributing to security measures and client communication.
Top Skills:
AnsibleAWSAzureBashBurp Suite ProC#CobaltstrikeGitlabMetasploitNessusPowershellPythonRubyTerraform
Healthtech
As Director Information Security, you will manage vulnerability remediation, collaborate with IT leadership, develop security strategies, and ensure regulatory compliance, while fostering automation and operational efficiency.
Top Skills:
Artificial IntelligenceAttack Surface ManagementAWSCybersecurity PrinciplesGCPHipaaHitrustInformation SecurityNist CsfPciVulnerability Management
Reposted 7 Days AgoSaved
Easy Apply
Easy Apply
Cybersecurity
The fellowship provides military spouses and separating service members with cybersecurity training and hands-on experience through projects and vendor training, aimed at enhancing their security skills.
Top Skills:
Information SecurityNetworkingSecurity Tools
Reposted 7 Days AgoSaved
Easy Apply
Easy Apply
Cybersecurity
Vulnerability Analysts at GuidePoint manage vulnerability programs, assess risks, communicate findings, and maintain positive customer relationships, while fostering a culture of continuous learning.
Top Skills:
ArmisAxoniusBashBigfixJAMFMac OsxPerlPowershellPythonQualysRapid7RbvmRhelServicenowSsmTaniumTenableUbuntu LinuxUvmWindows 10Windows 7Windows Server
Reposted 7 Days AgoSaved
Easy Apply
Easy Apply
Cybersecurity
GuidePoint Security seeks a SOAR Engineer to design, implement, and troubleshoot Palo Alto XSOAR solutions, manage SOC content, and utilize scripting for automation.
Top Skills:
BashJavaPalo Alto XsoarPerlPythonRegular ExpressionsScripting
Software • Cybersecurity • Data Privacy
The Security Engineer role involves managing identity governance, access management solutions, technical support of IAM technologies, and policy development.
Top Skills:
Active DirectoryC++CyberarkJavaJavaScriptLdapLinuxOktaPerlPowershellPythonQradarSailpointSplunkSQLVenafiWindows
Artificial Intelligence • Information Technology • Security • Automation
As an AI Security Context Engineer, you will translate security knowledge into actionable context for AI agents, improve investigations, and design multi-step workflows for threat detection and triage.
Top Skills:
AICloud Security LogsCloud-Native Ai StackEdrIpsSIEM
Food
The Lead Security Analyst will manage cybersecurity incidents, enhance response capabilities, and drive threat intelligence for the organization.
Top Skills:
Information SecurityIntrusion DetectionPenetration TestingPowershellPythonSecurity OrchestrationSIEM
Reposted 8 Days AgoSaved
Easy Apply
Easy Apply
Cybersecurity
The DFIR Consultant will support incident response and forensic investigations, perform threat discovery, communicate with clients, and utilize scripting to enhance efficiency.
Top Skills:
Amazon Web ServicesAzureBashEdrFwGoogle SuiteGoM365NdrNgavPowershellPythonSIEMVelociraptorXdr
eCommerce • Fintech • Information Technology • Payments • Software
As a Technology Security Analyst, you'll manage API security, collaborate with development teams, automate workflows, and ensure policies for API security are maintained.
Top Skills:
C#Java
Big Data • Healthtech
The Information Security Engineer will manage vulnerabilities, conduct penetration testing, support incident response, develop security automation, and promote security best practices across the organization.
Top Skills:
AWSAzureGCPLinuxmacOSPowershellPythonWindows
Big Data • Information Technology • Software • Energy • Big Data Analytics
As a Security Analyst II, you will secure the grid by automating security, conducting vulnerability management, monitoring cloud configurations, and supporting compliance audits.
Top Skills:
AWSAws InspectorAzureBashCloudFormationMicrosoft DefenderMicrosoft SentinelOracle CloudPowershellPythonQualysRapid7SplunkTenableTerraform
New
Track Smarter, Apply Better.
Ditch the spreadsheets. Organize your job search with our freeApplication Tracker.
Use For Free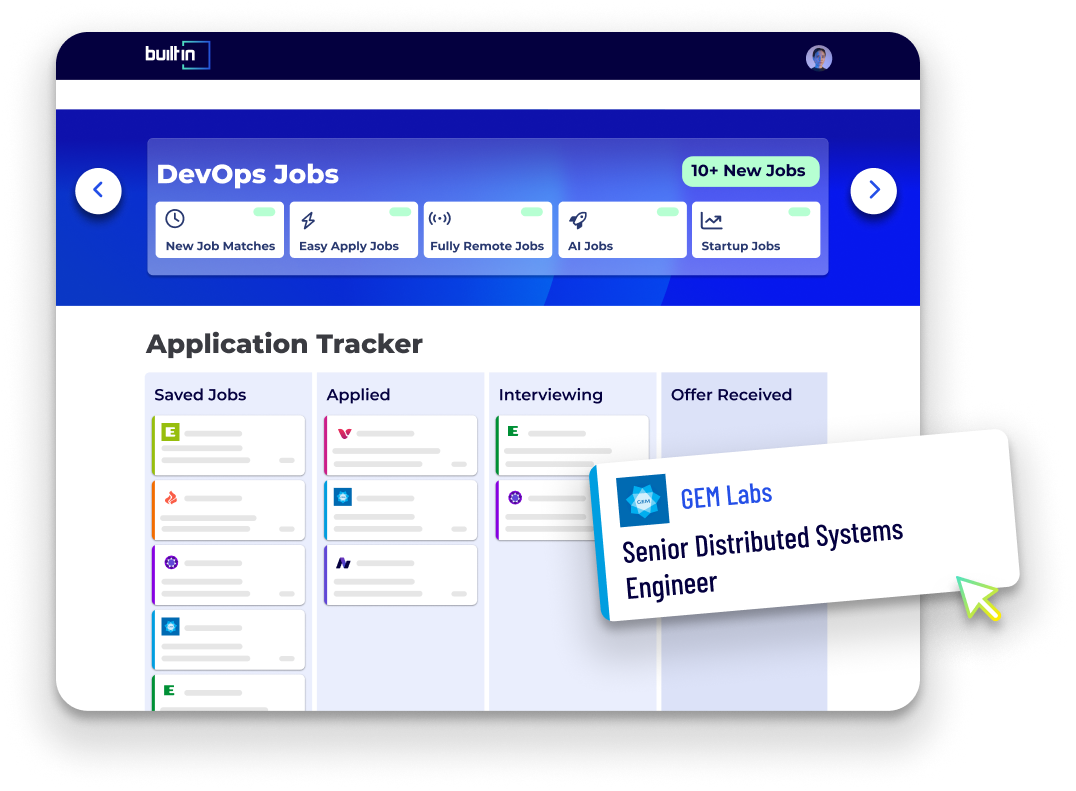
Security • Cybersecurity
The Cyber Defense Analyst is responsible for monitoring, investigating, and responding to security alerts, leading incident response, and improving automation in a hybrid environment.
Top Skills:
AWSBashCdrCspmEdrGitOktaPythonSIEMSoar
Reposted 9 Days AgoSaved
Artificial Intelligence • Blockchain
The role involves auditing blockchain products, improving security tools, conducting research, and enhancing security processes for smart contracts.
Top Skills:
GoRustSolidity
Information Technology • Insurance • Professional Services • Software • Cybersecurity
The Cyber Analyst role involves developing cybersecurity services, advising policyholders on cyber risk management, and collaborating with various teams to improve security posture.
Top Skills:
CybersecurityEdr
Software • Cybersecurity • Data Privacy
The Senior Cyber Security Engineer will enhance endpoint protection, data loss prevention, and identity security while mentoring junior staff and leading initiatives in a regulated environment.
Top Skills:
APIsAWSAzureCasbDlpGCPMicrosoft Defender XdrPowershellPythonSIEMSoar
10 Days AgoSaved
Easy Apply
Easy Apply
Cybersecurity
The PAM Engineer designs, deploys, and manages Privileged Access Management solutions, focusing on account security and compliance, while collaborating with various teams to implement secure practices.
Top Skills:
Active DirectoryAWSAzureAzure AdBeyondtrustCyberarkDelinea Secret ServerGCPPowershellPythonRest Apis
News + Entertainment
The Security Software Engineer will develop and improve detection frameworks to identify risks, utilizing detection-as-code and collaboration across teams.
Top Skills:
AWSHiveJavaPythonSQL
Cybersecurity • Data Privacy
The IAM Architect will deploy and support the Ping Identity platform, execute migrations, analyze infrastructure updates, assist clients, and engage in knowledge sharing.
Top Skills:
AWSGCPLdapAzureMicrosoft ServerOauthOpenid ConnectOraclePingaccessPingdirectoryPingfederateSAMLUnixWindows
Cybersecurity • Data Privacy
The role involves conducting health checks, managing deployments, running pilots, and giving recommendations on Microsoft security products.
Top Skills:
Azure Information ProtectionAzure SentinelEmsMicrosoft Defender For CloudMicrosoft Defender For EndpointMicrosoft For IdentityMicrosoft Information ProtectionMicrosoft IntuneOffice 365
Cybersecurity • Data Privacy
The IAM Business Security Architect will develop and deploy xIAM solutions, improve onboarding processes, and provide architecture advisory services for security operations.
Top Skills:
Api GatewaysCiamIamKerberosLdapMfaMicrosoft Active DirectoryOauthOidcOne Identity ManagerPing FederatePkiSAMLScimSoa ServicesSpmlXacml
Cybersecurity • Data Privacy
The Security Threat Intelligence Engineer will analyze security threats, produce intelligence reports, and enhance threat detection processes, ensuring cybersecurity resilience against diverse attacks.
Top Skills:
AWSAzureEdrElkGCPIdsMispSIEMSnowflakeSoarSplunkStixTaxii FrameworksThreat Intelligence FeedsThreat Intelligence Platform
Cybersecurity • Data Privacy
The role involves developing and improving threat detection systems, writing alert strategies, and supporting incident response teams. Requires collaboration and strong analytical skills to enhance security measures.
Top Skills:
AWSMS OfficePythonSIEMSoarSplunkSQL
Reposted 10 Days AgoSaved
Cybersecurity • Data Privacy
The Security CIAM Engineer will design, develop, and deploy CIAM solutions, focusing on identity lifecycle management and working within an agile team to enhance CIAM platforms.
Top Skills:
AWSAzure Active DirectoryGCPMS OfficeOkta
Cybersecurity • Data Privacy
The Data Protection Consultant will develop a Data Protection Program Framework, document processes, facilitate stakeholder agreement, and create a roadmap while managing data protection technologies and governance standards.
Top Skills:
AWSBigidGCPMS OfficeMs AzureMs365ThalesVaronisVormetric
Top Companies in Memphis, TN Hiring Remote Cyber Security Roles
See AllPopular Memphis, TN Remote Job Searches
Remote Jobs in Memphis
Remote Content Jobs in Memphis
Remote Customer Success Jobs in Memphis
Remote IT Jobs in Memphis
Remote Cyber Security Jobs in Memphis
Remote Tech Support Jobs in Memphis
Remote Data & Analytics Jobs in Memphis
Remote Analysis Reporting Jobs in Memphis
Remote Analytics Jobs in Memphis
Remote Business Intelligence Jobs in Memphis
Remote Data Engineer Jobs in Memphis
Remote Data Science Jobs in Memphis
Remote Machine Learning Jobs in Memphis
Remote Data Management Jobs in Memphis
Remote UX Designer Jobs in Memphis
Remote Software Engineer Jobs in Memphis
Remote Android Developer Jobs in Memphis
Remote C# Jobs in Memphis
Remote C++ Jobs in Memphis
Remote DevOps Jobs in Memphis
Remote Front End Developer Jobs in Memphis
Remote Golang Jobs in Memphis
Remote Hardware Engineer Jobs in Memphis
Remote iOS Developer Jobs in Memphis
Remote Java Developer Jobs in Memphis
Remote Javascript Jobs in Memphis
Remote Linux Jobs in Memphis
Remote Engineering Manager Jobs in Memphis
Remote .NET Developer Jobs in Memphis
Remote PHP Developer Jobs in Memphis
Remote Python Jobs in Memphis
Remote QA Jobs in Memphis
Remote Ruby Jobs in Memphis
Remote Salesforce Developer Jobs in Memphis
Remote Scala Jobs in Memphis
Remote Finance Jobs in Memphis
Remote HR Jobs in Memphis
Remote Internships in Memphis
Remote Legal Jobs in Memphis
Remote Marketing Jobs in Memphis
Remote Operations Jobs in Memphis
Remote Office Manager Jobs in Memphis
Remote Operations Manager Jobs in Memphis
Remote Product Manager Jobs in Memphis
Remote Project Manager Jobs in Memphis
Remote Sales Jobs in Memphis
Remote Account Executive (AE) Jobs in Memphis
Remote Account Manager (AM) Jobs in Memphis
Remote Sales Leadership Jobs in Memphis
Remote Sales Development Representative Jobs in Memphis
Remote Sales Engineer Jobs in Memphis
Remote Sales Operations Jobs in Memphis
All Filters
Total selected ()
No Results
No Results


























