We all get frequent requests to provide our personal information.
Some of these requests are absolutely important: entering another country, having a product shipped to your home, or receiving medical care. In these cases, we can and should willingly give our personal information to those requesting it.
Despite the exceptions, most of these requests are really unimportant: a nonprofit organization wants to contact you, you sign up for an online cooking class, or a reasonably cute human at a dive bar asks for your phone number. In these cases, we still give out the same personal information to those requesting it.
But we shouldn’t. Not ever.
Why? Because personal information is a top commodity in today’s digital world, and sharing it should be based on trust, not convenience. Instead of giving out details willy-nilly, I’d like to propose that we all take a page from a James Bond novel. So let’s learn how to use a bunch of mostly free tools to “classify ourselves” and help protect our personal information.
Setting Categories and Making a Plan
Classifying our personal data is a three-step process:
- We learn to establish two categories for requests: critical and non-critical.
- We evaluate each request for our personal data and decide its category.
- We create and share different personal data based on the kind of request we’ve received.
Once we have our plan, our main goal is to stick to it. For example, I only provide my personal email, cell phone or mailing address to close friends and family. By comparison, today, I got the following “offers” when visiting two websites:
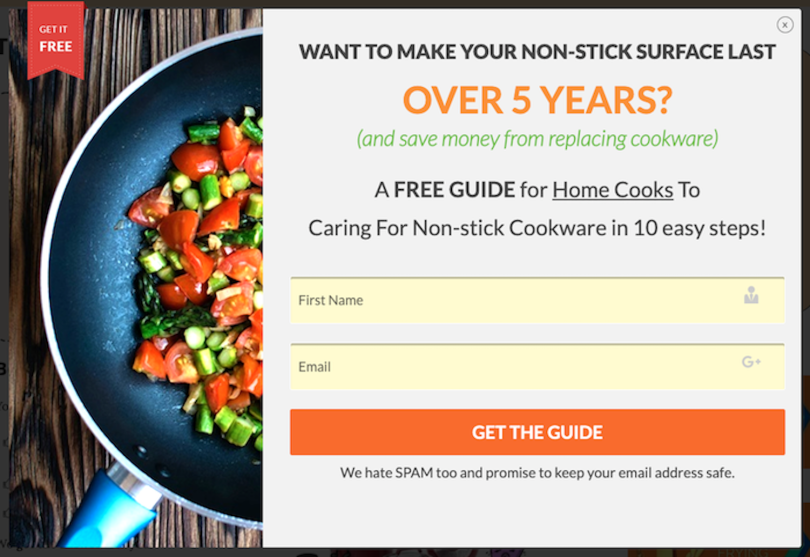
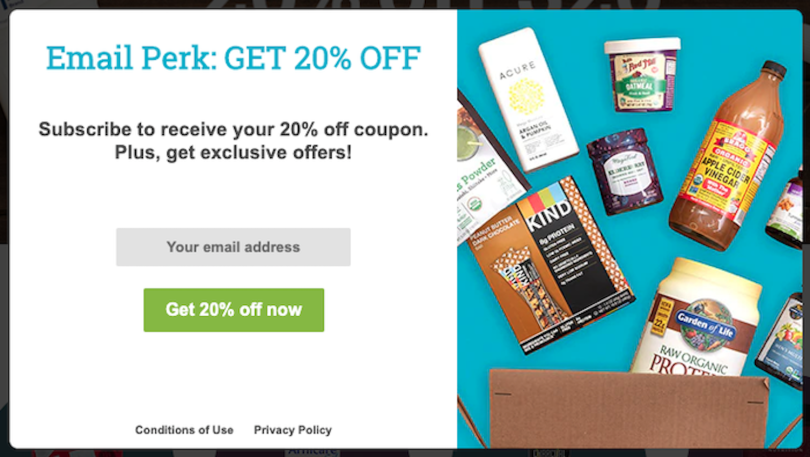
Now, look: I like getting 20 percent off as much as the next person, but I always follow my plan. As these are not critical communications, I wouldn’t provide my personal email address. Instead, I would use my secondary contact information for these kinds of requests.
Obtaining secondary data is 100 percent legal, 100 percent easy, and 100 percent necessary in today’s digital world to help guard our privacy. Now that we’ve established the necessity of creating secondary contact information, let’s find out what tools to use and how to use them.
Getting and Using Secondary Emails
When I send holiday cards to family and friends, I put my home address on the envelope. When I’m sending business-related materials, however, I put my business address on the envelope instead. My email strategy is no different: I maintain different email addresses for different reasons. I accomplish this with the free tool 33mail.com.
I discovered this service some years ago and was intrigued. Their service offers unlimited, free, customizable email addresses, a simple interface, and the ability to halt spam instantly. Even better, its operation is simple and getting started is easy.
First, you sign up and grab yourself an account name — let’s say, “SoniaStopsSpam.” Then, when any non-critical person or service “needs” your email, don’t provide your personal email address. Instead, give them a custom 33mail.com email address that’s built from your 33mail account name. For example:
You’ll still get all of your emails from that company (or person), but they’ll be forwarded from 33mail.com to your personal email address. Reply to those emails just as you would any other email. Then, if the time comes when you’ve decided that you no longer want emails from that account, ending the stream is a piece of cake. Click the link you’ll see at the top of every 33mail message:
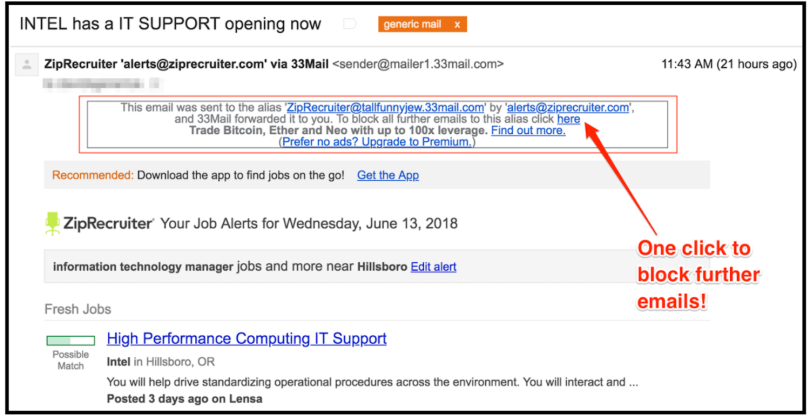
That’s it. The free, basic tier is enough for most casual users, but I’ve enjoyed the service so much that I signed up for the $1/month paid tier. The extra $1 month removes the ads that 33mail includes in the free version, allows an additional 40MB of data in my email relays, along with the ability to use my own domain if I want to, which are all nice features.
Getting and Using Secondary Phone Numbers
If you needed another reason to not give out your personal cell number to strangers, here it is: Americans received 58 billion robocalls in 2019. That’s billion. With a “B.” That’s roughly 175 calls to every single American over the course of the year.
I don’t like spam calls, so I use a secondary, virtual phone number for any person I don’t know and for all organizations. Here’s how you can as well.
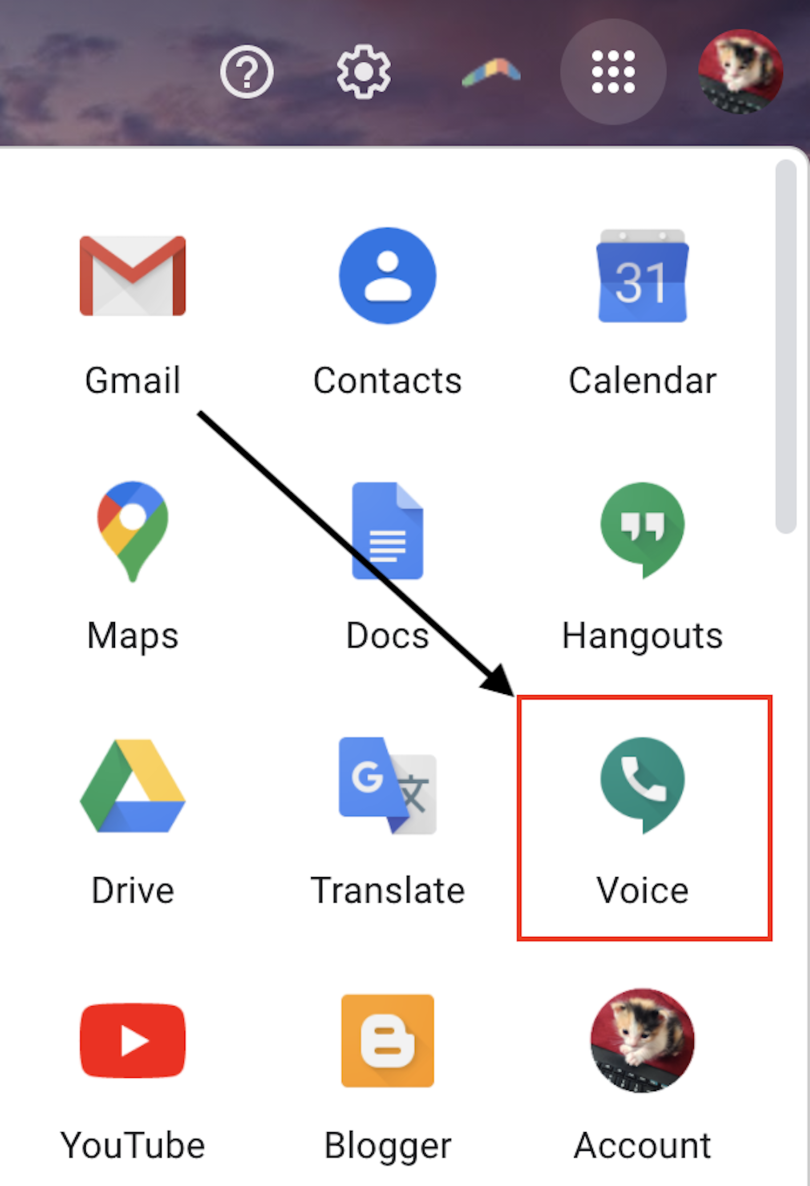
Google Voice works on all computers and Chromebooks as well as any tablet or smartphone running iOS or Android. The service is free, easy to use, integrates seamlessly into Google’s ecosystem, and offers two of the best features that Google pioneered: a powerful search engine and effective spam filtering for your phone calls. Getting to Google Voice is easy if you’re logged into your Google account in a web browser: just click the “dialpad” icon and then click “Voice” from the dropdown menu as shown. Note, though, that mobile apps are available for those not using a computer.
The first time you log in, you’ll need to pick a phone number, record a personal voicemail greeting and then ... that’s it! Start giving out your Google Voice number to anyone who isn’t a close friend or family member. This virtual number works for phone calls and text messages, even those with attached photos. You can forward texts and calls to your actual cell phone if you like, or you can choose to leave them on Google’s servers. Either way, nobody using your virtual number will ever know the difference.
Also, if you’re wondering why a security/privacy writer like myself would recommend a product from Google — a company known for harvesting data about you from its free services — just remember: If you’re using this number only for people or organizations you don’t know or trust, then you’ll only be feeding Google data that isn’t central to your life.
Getting and Using Secondary Mailing Addresses
Most of us forget that we’re under no obligation to provide our home address to anyone. In fact — depending on the circumstances — United States citizens might not even need to provide their residential address or ID to the police if they ask. This fact raises the question: Should we ever provide our actual, residential address to anyone?
To family and friends, absolutely. To everyone else, definitely no.
Instead, if you’re employed by a company, use the company’s address. That’s the easiest option, and it’s free. Otherwise, most local post offices offer P.O. boxes, as do public corporations like UPS. You can expect to pay at least $100 to $150 per year for smaller mailboxes, and you’ll also have to travel from your home to these secondary locations to pick up your mail.
But why bother leaving your house to get your mail? Especially now, during a pandemic? Instead, let me share an even better solution.
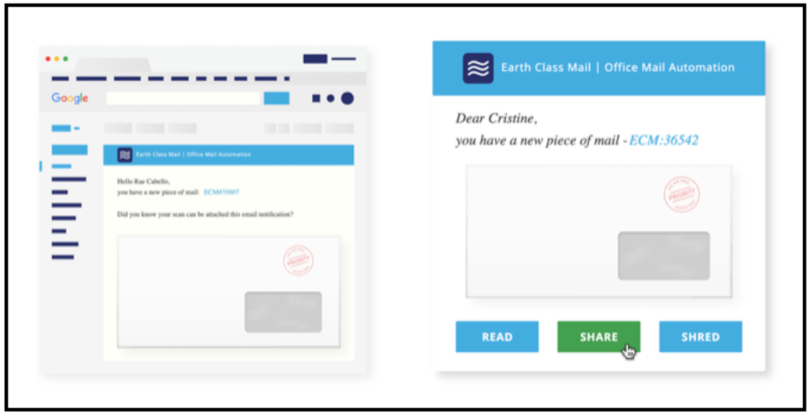
How does the idea of having an address in another city sound? What if I told you that all the mail sent to that address could be opened, scanned to PDF, and then emailed to you wherever you actually are? Sounds pretty spy-tastic, right? Well it’s real, and it’s called Earth Class Mail.
My family used Earth Class Mail for several months when I started a tech job at Nike, which required a move to a different city and, therefore, a new address before we found a place to live. I found the service easy to use, extremely convenient, and very secure. They offer HIPAA compliance standards with yearly recertification, mandatory employee background checks, and 24/7 video surveillance of the scanning facility.
Not bad for a service with monthly fees that currently start at $19.
You call the shots on your physical mail: any of your letters can be stored for later use, unimportant items can be trashed or recycled, checks can be deposited (#MindBlown), scanned items can be shared with anyone you wish, and original documents you need physically can be mailed to your actual physical location, wherever that may be.
By changing how you respond to requests for your data and by leveraging the power of secondary email addresses, phone numbers, and mailing addresses, you’ll certainly increase your privacy, security, and peace of mind.
Best of all, most of the tools available for this approach are 100 percent free.





