Penetration testing can prove extremely useful in identifying security vulnerabilities attackers can exploit. When you are looking for a vendor to conduct a penetration test, it’s important to understand the different phases of a proper test.
What Is a Penetration Test?
What Is Penetration Testing?
Penetration testing is the method of simulating a cyber attack to detect security vulnerabilities within a system. This allows businesses to see whether their security infrastructure can withstand various types of attacks and the implications of a successful attack. The person leading this exercise should be unfamiliar with a company’s security setup, so organizations often hire contractors known as ethical hackers to execute penetration testing.
The general rule is that companies should conduct penetration testing at least once a year. By following this practice, IT and security teams can ensure their security systems are up-to-date and address any weaknesses before actual hackers exploit them.
Phases of Penetration Testing
Penetration testing is broken up into seven stages to maintain a thorough process and help businesses glean as many insights as possible about their security systems.
What Are the 7 Phases of Penetration Testing?
- Pre-engagement
- Reconnaissance
- Discovery
- Vulnerability Analysis
- Exploitation
- Reporting
- Remediation
1. Pre-Engagement
The pre-engagement phase consists of discussing and agreeing on scope, logistics, rules of engagement and timeline. Understanding what you want tested and why is important before entering discussions with vendors.
Choose the Type of Penetration Test
There are many different types of penetration tests:
- Internal and External Network
- Application
- Wireless
- Physical
- Social Engineering
Depending on the type of testing, the tester may be required to travel to a physical office location (as in wireless or physical testing). Other types of testing may be conducted remotely, such as network or web application testing.
Define the Scope
Practically speaking, defining your scope will allow you to prioritize the assets tested and will often have a direct connection to pricing. The scope of a test depends on what exactly you’re testing. If you’re conducting a network penetration test, you should know which IPs or subnets you want tested. If you are conducting an application penetration test on the other hand, you should know the size and complexity of the application, including how many different user roles you want tested.
Establish the Timeline
Every penetration test must also have a defined timeline. This is because these tests don’t always have a defined end-state, so you’ll want to define the duration of the test explicitly with the vendor. Moreover, you’ll need to define the testing scope before the timeline, as the scope can greatly affect the duration required to properly test the assets. For example, an internal network penetration test on 50 active IPs will require a shorter timeline than 500 IPs for the same level of intensity.
Set the Rules of Engagement
Finally, rules of engagement are a formal contract between the tester and the organization receiving the test. Because many of the actions a penetration tester takes are illegal without explicit authorization, rules of engagement outline exactly what the tester is and isn’t allowed to do on your network. Any actions you don’t want taken need to be explicitly outlined in this contract (which will differ across organizations). It is also useful to list any critical assets in this contract to which the testers should pay extra attention.
2. Reconnaissance
The reconnaissance phase consists of open-source intelligence (OSINT) gathering techniques to better understand the target organization and network. You’d be surprised what information you can freely gather from open sources.
Sources commonly used to gather information include social media such as LinkedIn, the organization’s public website, and media and PR documents. You may ask — but how is any of this information useful?
LinkedIn, for example, provides a great place to scrape employee information. Understanding the names and roles of employees in the organization can aid in enumerating email addresses for a phishing attack or identifying network administrators.
Attackers can gather network information using open-source tools such as Shodan or Censys. These tools continuously scan public-facing IP addresses and index their response headers. This allows the tester to begin building a picture of the external network without having to actively scan it.
3. Discovery
The discovery phase consists of scanning and asset analysis. Typically, the tester will use a network scanning tool such as nmap to identify which assets are available and to gather some basic information about them such as operating system, open ports and running services.
Here’s the output of a basic nmap scan for a single host.
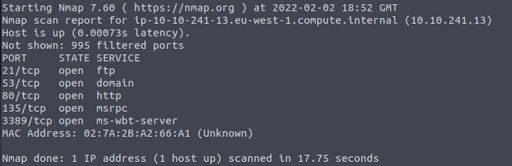
The penetration tester may or may not already have a list of targets by IP. In a white box test, targets and some asset/network information are provided and available to the tester. A black box test, on the other hand, starts with little to no information about the targets or network, with the tester usually only having a domain or organization name. In a black box test, however, it’s still good practice to provide the tester with an asset inventory and scope guidelines for the purpose of confirming ownership before they take any actions.
4. Vulnerability Analysis
After testers scan and analyze assets, they’ll use vulnerability identification methods to look for potential exploitation opportunities. Testers may identify vulnerabilities manually by analyzing the results of the previous discovery phase and utilizing existing knowledge, but they’re more likely to use an automated vulnerability scanning tool.
There are many vulnerability scanning tools available, and they’re often used by organizations as part of a continuous vulnerability management program. Some popular tools include Tenable, Rapid7, and Qualys. Even nmap has some vulnerability scanning capabilities tests can use during the discovery phase.
Here’s an example output from an nmap vulnerability scan against a single host.
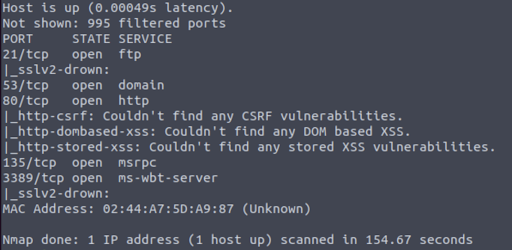
5. Exploitation
After testers have identified vulnerabilities, attackers will attempt to exploit those vulnerabilities using either public or custom exploits. Generally, the ultimate target is root or administrator privileges on a machine, especially a domain controller.
A common tool used for this is Metasploit, a framework that provides a streamlined process for finding and executing publicly available exploits for vulnerabilities.
The exploitation phase is the key differentiator between a penetration test and a vulnerability scan. Vulnerability scans will identify vulnerabilities on the network, but can come with some caveats. They may identify false positives or exploit code that isn’t applicable to that individual environment.
In a penetration test, however, the tester will exploit the vulnerability and prove that the vulnerability is actually exploitable, as well as simulate the ramifications of exploiting that machine — such as data exfiltration.
For example, an asset may have been identified as low-risk due to the lack of sensitive information stored, transmitted or processed by the asset, but exploitable vulnerabilities proved to allow the attacker to pivot (move from one machine to another) through the network from that device.
6. Reporting
Reporting is arguably the most important phase of any penetration test. You’ll want to investigate the reporting standards of a vendor before moving forward with a test. One way to do this is by requesting a sanitized example report.
During the reporting phase, the tester will put together a report outlining the test, including a narrative of the attack chains executed. A good penetration test report will have the findings well-organized and prioritized by risk level. They should provide screenshots and detailed descriptions so you can reproduce the issues during the remediation phase. Most testers will also provide guidance on how to remediate their findings.
A typical penetration test report will consist of the following sections:
- Executive Summary
- Methodology
- Detailed Findings and Recommendations
- Appendices (usually including a vulnerability report in spreadsheet format)
7. Remediation
The remediation phase is usually in the organization’s hands; it’s up to them what they do with the findings and whether or not they close the identified gaps.
Generally, an organization will take the penetration testing report and attempt to reproduce and validate the attack chains. Then, they’ll implement the appropriate changes using a combination of public sources, employee knowledge and the tester’s remediation guidance.
While remediation may sound straightforward, it can be more difficult than you would think. Before making any domain-wide changes to the environment, it’s best to adopt a rollout testing process, starting with a small, diverse subset of test users or devices with documented and tested rollback procedures in the event the change breaks business processes.
The Takeaway
Penetration tests are an important piece of your organization’s security program by helping identify exploitable vulnerabilities and prioritize remediation. However, choosing a vendor to conduct the test isn’t always easy. Understanding the seven phases of a penetration test is critical for an organization to properly engage and understand the service they’re buying.
Opinions expressed are solely my own and do not express the views or opinions of my employer.
Frequently Asked Questions
Why is penetration testing important?
Penetration testing is important for helping IT and security teams determine whether their systems are prepared to handle different types of cyber attacks. If weaknesses are found, teams can upgrade their security infrastructure and take a more proactive approach to cybersecurity by removing vulnerabilities before hackers discover them.
What are the stages of penetration testing?
Pre-engagement, reconnaissance, discovery, vulnerability analysis, exploitation, reporting and remediation are the stages of penetration testing.
What is the difference between penetration testing and vulnerability scanning?
Vulnerability scanning is a quick, automated test that merely seeks to identify potential weaknesses in a security system. Penetration testing is much more in-depth since a human actively tries to exploit any openings in a company’s security defenses and demonstrate the ramifications of a successful cyber attack.





