Get the job you really want.
Maximum of 25 job preferences reached.
Top Cybersecurity Jobs
Financial Services
As Head of Cybersecurity Operations, you will manage a team, develop strategies for security monitoring, and respond to high severity incidents, fostering a security-first culture across the organization.
Top Skills:
CybersecurityInformation TechnologyMitre Att&Ck Framework
Fintech
Responsible for leading vulnerability management, developing teams, ensuring security measures align with business goals, and communicating risks to stakeholders.
Top Skills:
Cloud-Native EnvironmentsCybersecurityDevOpsDevsecopsFfiecIso 27001Nist CsfSecure Development PrinciplesSecurity Posture PlatformsVulnerability Management
Information Technology • Software
The role involves supporting a mission-critical program by developing system engineering documentation and conducting cybersecurity evaluations. Responsibilities include technical support, requirements assessment, and managing security risks while ensuring compliance with certification processes.
Top Skills:
CybersecurityInformation AssuranceSystems Engineering
Consulting
As a Consultant, you will support clients by improving business processes and internal controls, while developing client deliverables and engaging with senior management.
Top Skills:
CybersecurityFismaInformation TechnologyNessusNistUnixVulnerability ManagementWindows
Information Technology
The IA Analyst will develop and maintain cybersecurity policies, conduct RMF compliance, manage accreditation documentation, and support cloud transitions, ensuring adherence to Air Force directives and cybersecurity standards.
Top Skills:
Afi Series 33Cloud ComputingCybersecurityDisa StigsEmassRisk Management Framework
Information Technology
The Information Systems Security Analyst will implement cybersecurity controls, conduct assessments, support the RMF lifecycle, and advise on risk posture.
Top Skills:
AcasCybersecurityInformation AssuranceRisk Management Framework (Rmf)StigVramVulnerability Scanning Tools
Information Technology
The Cybersecurity Analyst monitors and investigates security incidents, conducts risk assessments, and maintains security documentation, focusing on protecting an organization’s information assets.
Top Skills:
CybersecurityInformation Security Management SystemsNetwork Security DocumentationRisk Assessment
Aerospace
The ISSO will manage cybersecurity for the STARE Program, including project management, compliance, administrative support, and developing relationships, while requiring a Secret Clearance.
Top Skills:
AcasCybersecurityEmassEvaluate_StigInformation TechnologyNist Sp 800-53Risk Management FrameworkScapStig Viewer
Reposted YesterdaySaved
Information Technology • Software
The internship program offers hands-on experience in IT, AI, Data Analytics, and Cybersecurity, alongside mentoring and networking opportunities with executives.
Top Skills:
Artificial IntelligenceAws)Cloud (AzureCybersecurityData AnalyticsInformation TechnologyMicrosoft Office SuitePower BISQL
Aerospace
The role involves serving as a Senior ISSE to perform assessment and authorization tasks related to cybersecurity compliance, risk assessments, and maintaining Authorizations to Operate for DoD medical systems.
Top Skills:
AppdetectiveAssured Compliance Assessment SolutionCybersecurityDisa StigsEmassFortifyInformation TechnologyNist 800-53Risk Management FrameworkWebinspect
Financial Services
The Lead Cybersecurity Architect at JPMorganChase develops cybersecurity solutions, engages teams to propose technical approaches, leads evaluations, and advocates new technologies while fostering diversity and inclusion.
Top Skills:
Agile MethodologiesAutomationCloud Native TechnologiesContinuous DeliveryCybersecurity ArchitectureProgramming Languages
Automotive • Cloud • Greentech • Information Technology • Other • Software • Cybersecurity
The Principal Cybersecurity Integrated Architect leads cybersecurity architectural standards, advises engineering teams, mentors peers, and mitigates threats in multi-cloud and on-premises environments.
Top Skills:
.NetAgile MethodologiesAWSCloud Enterprise SolutionsContainerizationCryptographyCybersecurity FrameworksDevsecopsEcsEksFargateIaasIamJavaLambdaOraclePaasPythonSaaSSecurity ProtocolsSpring FrameworksVirtualizationZero Trust
New
Track Smarter, Apply Better.
Ditch the spreadsheets. Organize your job search with our freeApplication Tracker.
Use For Free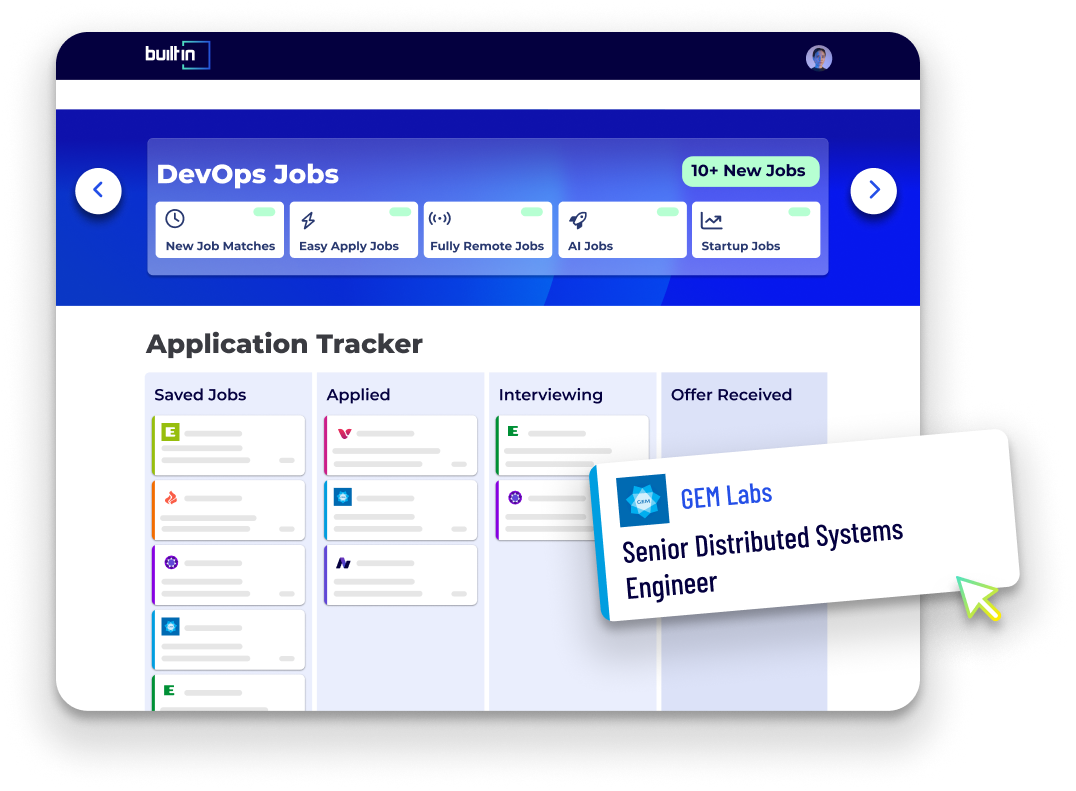
Automotive • Cloud • Greentech • Information Technology • Other • Software • Cybersecurity
The Principal Cybersecurity Integrated Architect leads cybersecurity architecture, advises teams on secure product development, and fosters compliance with security standards.
Top Skills:
.NetAWSContainerizationDevsecopsJavaOraclePythonSpring FrameworksVirtualization
Healthtech
As Chief Information Security Officer, lead and manage global security strategy, ensuring compliance and security across all company functions and respond to security incidents.
Top Skills:
CobitCybersecurityEpic Electronic Medical RecordsGrcIdentity ManagementIso 27001Nist CsfSecurity OperationsSoftware Security
Automotive • Information Technology
The Head of Security Strategy and Planning oversees strategic, operational, and financial planning for the Security Department, ensuring alignment with business objectives and project management for security initiatives.
Top Skills:
Business AdministrationCismCisspCybersecurityInformation TechnologyIso 27001Nist CsfPmpPrince2Risk ManagementSoc2
Reposted YesterdaySaved
Security • Software
This is a general application for various roles in cybersecurity, IT support, help desk operations, and field technician services, inviting applicants to submit their resume for future opportunities.
Top Skills:
CybersecurityField Technician ServicesHelp Desk OperationsInformation TechnologyManaged Service Provider Support
Transportation
The Cybersecurity Analyst will support incident response, track remediation of findings from the SOC, conduct training, and enhance security posture at BETA Technologies.
Top Skills:
CybersecurityIncident ResponseInformation SecurityVulnerability Management
Artificial Intelligence • Information Technology • Internet of Things • Software • Automation
The Detection Analyst will analyze incidents, review alerts, collaborate with teams, and use various cybersecurity tools to ensure information security.
Top Skills:
CybersecurityData Loss PreventionDigital GuardianEncaseInsider ThreatMagnetRmsSecuronixSiem ToolsSureviewUba
Security • Cybersecurity
The Cyber PM manages cybersecurity aspects for non-enterprise IS under Department of Defense programs, ensuring compliance and effective risk management while coordinating with stakeholders and contractors.
Top Skills:
CybersecurityFismaRisk Management Framework
Automotive • Cloud • Greentech • Information Technology • Other • Software • Cybersecurity
The Senior Cybersecurity Engineer will enhance security architecture, manage access control, oversee incident response, and drive compliance initiatives while collaborating with cross-functional teams.
Top Skills:
AWSAzureBashDnsEdrFirewallsGoogle Cloud PlatformJavaScriptLoad BalancingNode.jsPerlPowershellPythonRubySIEMVpn
Automotive • Cloud • Greentech • Information Technology • Other • Software • Cybersecurity
The Senior Cybersecurity Engineer will enhance security architecture, manage identity and access, oversee incident response, and collaborate on security strategies to align with business objectives.
Top Skills:
AWSAzureBashDnsEdrFirewallsGoogle Cloud PlatformJavaScriptNode.jsPerl)PythonRubyScripting Languages (PowershellSIEMVpn
Robotics • Analytics • Energy
The role involves delivering cybersecurity solutions for operational technology environments, ensuring compliance, and providing customer training and support throughout the implementation process.
Top Skills:
Av SolutionsCybersecurityIcsIec 62443Iso/Iec 2700XModbusNetwork MonitoringNistOpcScada
Reposted 2 Days AgoSaved
Design
As a Cybersecurity Analyst II, you'll implement security measures, analyze risks, oversee recovery plans, and ensure system security for government missions.
Top Skills:
AcasCasp+CisspCybersecurityHbssIamLinuxNist 800-53RmfSecurity+SIEMWindows Administration
Security • Cybersecurity
The Exploitation Analyst will develop plans, oversee Red Team operations, identify gaps, and coordinate with DoD on cyber capabilities.
Top Skills:
Computer ScienceCybersecurityMicrosoft Office Applications
Other
Lead cybersecurity efforts for TRADOC G2 operations, ensuring compliance with DoD RMF and protecting mission data from cyber threats.
Top Skills:
CybersecurityDisa StigsDod Risk Management FrameworkIncident ResponseIt InfrastructuresVulnerability Assessments
Top Companies Hiring Cybersecurity Roles
See AllPopular Job Searches
All Filters
Total selected ()
No Results
No Results
































