Who are you? Websites ask that all the time, though not in so many words. Instead, they require passwords, or your mother’s maiden name or a code sent via text. Sometimes you also have to prove you’re not a robot by deciphering distorted letters.
These authentication efforts are all part of a new cybersecurity ethos called “zero trust,” one pillar of which is this: Never assume you know someone’s true identity based on just their IP address or email password. Hence the growing popularity of identity management solutions like multi-factor authentication.
Top Identity Management Solutions
- SailPoint’s Identity Platform
- Oracle Identity Management
- Okta Identity Management
- OneLogin’s Trusted Experience Platform
- Microsoft Azure’s Active Directory
- Google’s Cloud Identity
- AWS’s Identity & Access Management
- EmpowerID
- Rippling
- LastPass Enterprise
Another zero-trust pillar: No one should have access to information they don’t need. That may seem obvious, but it wasn’t always. Once upon a time, castle-and-moat style security architecture reigned. Rather than containing breaches, it focused on keeping outsiders out — which meant that a valid login from anyone, even an entry-level employee, granted total access to workplace networks. That made life easy for moles and hackers who, with a single login, could do major damage.
That's not the case in a zero-trust system, where users must prove they are who they claim to be before gaining access to information they need to do their jobs — and nothing more. An account executive, therefore, has different privileges than an engineer, who has different privileges than a user-experience designer. In the most sophisticated systems, privileges vary over time, too — so a user might have access to a classified database only at certain hours of the day.
Enforcement, however, requires sophisticated software ranging from encrypted password managers to elaborate IT-and-HR platforms. Here are 19 of those identity management solutions.

Location: Austin, Tex.
Sailpoint’s Identity Platform: Wherever sensitive data lies, SailPoint’s identity governance platform keeps tabs on who could access it, who actually accesses it and what they do with it. The latest version of the platform also helps IT allocate permissions, with machine learning algorithms that learn how organizations work and recommend title-appropriate privileges for new users. While the suggestions aren’t perfect, they’re always improving thanks to what SailPoint’s Mike Kiser calls a “virtuous loop” between human and machine intelligence. Essentially, the algorithms handle easy decisions, which frees up humans to focus on harder decisions, which then inform and improve the SailPoint algorithms.

Location: Redwood Shores, Calif.
Oracle Identity Management: Part of Oracle’s middleware family, Oracle Identity Management offers an array of scalable tools for crafting user directories, personalizing user access and more. Together, these tools can manage the entire lifecycle of a login credential, from when it’s created and granted permissions to when it’s retired. Oracle offers cutting-edge user authentication, too, that’s based on passwords as well as typical digital behavior — how the user moves their mouse, say, or how quickly they type — which offers an added layer of protection against hackers and bots.
Location: San Francisco
Okta Identity Management: Okta offers two identity management systems: Workforce Identity (for employees) and Customer Identity. The two obviously have different features, but both offer Okta’s easy-to-implement adaptive multi-factor authentication (MFA) — essential in a threatscape where stolen credentials account for more than 80 percent of data breaches. The adaptive MFA basically assesses the risk-level of each login attempt, and requires more authentication for riskier situations — a user checking in from, say, a new device or a new country. Depending on context, logging in could be as simple as entering a password, or it could require a combination of password, a security question and a fingerprint.

Location: Redmond, Wash.
Microsoft Azure’s Active Directory: With a single sign on, Microsoft Azure’s Active Directory allows users to access more than 2,800 SaaS apps, from Salesforce to Canvas — provided they’re cleared to access them, of course. Azure AD also lets IT personnel customize access to sensitive materials and outline conditional access protocols. (For example: “This user should have access to this app only while connected to this network after providing two-factor authentication.”) Built for flexibility, the platform accommodates users including employees, partners and customers, accessing Cloud or on-premise servers.

Location: Mountain View, Calif.
Google’s Cloud Identity: Google’s Cloud Identity streamlines both the end-user experience and identity governance duties. It lets users access a universe of more than 5,000 apps with a single sign-on; meanwhile, IT leadership can manage their organization’s authorized users, apps and devices in a single interface. Google secures this convenient design with constantly updated threat intelligence and Beyondcorp, a zero-trust security solution that mandates encryption and multi-factor authentication. According to Google, Cloud Identity lets employees work remotely on any device from anywhere in the world, all without posing an unmanageable security risk.

Location: Ann Arbor, Mich.
Used by WhatsApp and Etsy, Duo Security was designed with modern companies in mind. That means it prioritizes speed. The DuoMobile app, for instance, simplifies multi-factor authentication. Users can merely tap on a push notification instead of typing in an SMS code to complete their login. Duo also allows for a modern, mobile-friendly work culture by letting organizations run security assessments on devices they don’t manage, including employee smartphones.
Location: Chicago
Keeper Security Enterprise: Think of Keeper Security Enterprise as a grown up version of Keeper’s free password manager. Like the free version, it generates random alphanumeric passwords for every new platform a customer accesses and stores them in an encrypted digital vault. With Keeper Security Enterprise, though, the encrypted vault stores more than passwords — users can also stash other confidential digital material, from metadata to encryption keys. They can share passwords to other users’ vaults, too, and chat on Keeper’s secure messenger service. And thanks to the role-based access controls and the platform’s compliance with such privacy standards as GDPR and HIPAA, IT managers can rest easy.

Location: New York City
Dashlane Business: Dashlane’s identity management tool for businesses is so comprehensive, users don’t even need to log out when they go home for the day. Instead, employees can divide their accounts into separate “Smart Spaces” for their personal and work passwords. That means Dashlane protects its users wherever they go online, autofilling relevant passwords as needed. It even scans the dark web, alerting users to any leaked passwords or personal information.

Location: Redwood City, Calif.
HID’s DigitalPersona: DigitalPersona software, one of HID’s many identity management offerings, takes multi-factor authentication to new heights. The basic premise remains the same: The more independent types of authentication required to log into a system, the more robust its security. However, DigitalPersona offers an unusual array of authentication types. Users can proffer passwords and answer security questions to log into Cloud, mobile and on-premise environments — but they can also use Touch ID, facial recognition, Apple Watches or bluetooth devices.

Location: San Francisco
OneLogin’s Trusted Experience Platform: As the name suggests, OneLogin lets users log into a multitude of popular apps — including the Google Suite, Workday and Mailchimp — with a single set of credentials. This doesn’t create the same vulnerabilities as manually reusing a single password, though. That’s thanks to OneLogin’s high-tech security features. Vigilance AI, for instance, employs behavioral analytics and other variables to scout for risky logins and the Shield browser extension screens every website users visit to flag phishing attempts.

Location: Seattle
AWS’s Identity & Access Management (IAM): Amazon’s IAM allows for extremely granular privilege settings. Administrators can require multi-factor authentication — pretty standard — but they can also give a user (or group of users) access to sensitive data only at certain hours of the day, or only when they’re using desired forms of encryption. To make privilege allocation easier, Amazon’s IAM integrates with institutional directories — and it’s built into every AWS account, free of charge.
Location: Dublin, Ohio
EmpowerID is all about giving users choices. Like many identity and access management solutions, it allows users to access all their apps via a single sign-on. It adds an extra layer of customizability, though: users can choose which of their existing credentials becomes their universal login. A user could, for instance, “empower” their Microsoft, Facebook, or Google logins to be universal logins. IT managers, too, enjoy a kind of universal login on the platform: They can customize user privileges across multiple sites from a single dashboard.
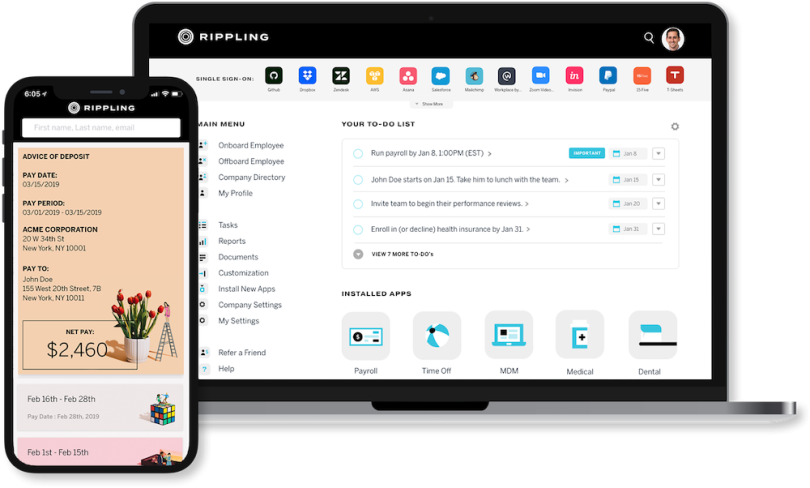
Location: San Francisco
Rippling fuses HR & IT into a single, scalable digital system. That might sound like a random combination at first, but it’s a major timesaver. Hiring a new employee, for instance, involves innumerable small-but-important HR and IT tasks. The hire must be added to the company directory and payroll. They need a computer and login credentials, as well as appropriate privileges for various apps. Rippling’s streamlining automation ensures that HR and IT always work in lockstep so an employee’s IT privileges grow with each promotion and expire on their last day.

Location: Boston, Mass.
LastPass Enterprise: LastPass may be best known for its free, encrypted password manager, but the company also makes a paid identity management solution that’s used by more than 60,000 businesses. The comprehensive Enterprise version blends LastPass’s signature hard-to-hack passwords — encrypted at the device level, rather than the centralized Cloud level — with a bevy of other features, including a single sign-on for more than 1,200 apps, safe password-sharing between employees and detailed security reports for IT.

Location: Pleasanton, Calif.
ZohoVault: This password manager from Zoho Corporation secures passwords with AES-256, the “gold standard” of encryption that’s used the U.S. government. The vault also allows users to safely share passwords with flexibly configured groups, easily modified as employees join and leave organizations. For maximum transparency, it tracks activity around the clock, logging who accesses which passwords when.

Location: Denver, Colo.
Ping Identity offers all the hallmarks of an identity management system, including single sign-on access to countless apps, multi-factor authentication and customizable permissions. But its most noteworthy offering might be intelligent API security. APIs, or application programming interfaces, play a central role in the integrations and plug-ins we all take for granted; they let developers build tools like, say, Google Maps into non-Google apps. However, APIs also create security risks. Ping Identity offers a solution: machine-learning algorithms that monitor API traffic closely, pinpointing security issues like token thefts and bot attacks.

Location: Pleasanton, Calif.
ManageEngine’s ADManager Plus: Designed for Windows systems, this active directory manager lets administrators automate common IT tasks such as creating new users and giving them appropriate access privileges. Done manually, these tasks chew up time and are prone to user error. With the help of automated templates, though, they require only a few clicks. ADManager Plus streamlines IT in other ways, too. For instance, its all-in-one console lets administrators manage their Microsoft Exchange Server and Windows Active Directory settings at the same time, without toggling back and forth between windows.
Location: Dublin, Ireland
Kaseya’s AuthAnvil: Designed for management service providers, or MSPs, AuthAnvil gives its clients security infrastructure they can pass on to their clients. It’s security-as-service, rooted in the Azure Cloud, that offers single sign-on access to multiple apps. It’s backed by two-factor authentication that forestalls phishing attempts, which means that even a stolen password is insufficient for an unauthorized login. AuthAnvil also lets administrators implement organization-wide password policies through a password manager.

Location: Aliso Viejo, Calif.
One Identity’s Identity Manage: In addition to attracting Fortune 100 clients like Chevron and American Express, this identity management solution earned a spot in Gartner’s 2019 Magic Quadrant for Identity Governance and Administration. That’s due in part to its unified approach to identity governance. Administrators can use One Identity to allocate privileges to any and all users, from entry-level hires to executives, across an array of apps and cloud providers (it integrates with Google, Azure and ServiceNow, among others). All the while, it tracks activity and allows for real-time security incident reports and risk heatmaps.